Has this situation ever happened to you? You enter search keywords in Google for a very specific topic. In the resulting screen, you see the title of that perfect article with exactly what you were seeking. Hopeful, you click the link and receive a 404-error message saying that the page does not exist. This scenario sadly happens to everyone countless times. Fortunately, there are two ways to view these once accessible pages.
Read the rest of this entry »
As a hacker, I have to program my remote web server to automatically perform routine tasks for me. It’s a whole lot easier and cheaper to rely on my web hosting company to manage an always-on server. For starters, I don’t have to pay for the 24/7 electricity the on-call technician!
To make the server perform an automated task in a Linux or Unix environment, you need to schedule a cron job. I won’t go through all the details of setting it up in shell terminal since most people do not have remote shell access. You can read about the details more at the cron and crontab Wikipedia articles. Most of us deal with an interface on the cPanel that looks kind of like one of these two screens.
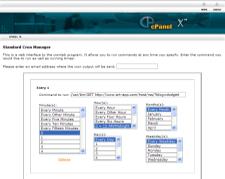
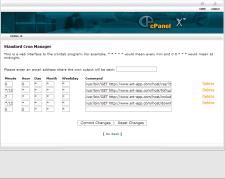
Read the rest of this entry »
The are a couple of things that are essential to any hacker’s walk of life. To name a few, there’s the ubiquitous flash drive for data transfer. You have the crossover cable for even faster data transfer. There’s the WiFi antenna for high gain and strong amplification. Possibly, you might find a video capture card in the computer. Of course, there’s the ubiquitous laptop and desktop computer. But what software is on these computers? Undoubtedly, you will find at least two operating systems, most often Windows and Linux. But with Linux, there are several different distributions. Is there a specific one? With hackers and crackers, there is only one Linux distro out there. It is called Backtrack.
Read the rest of this entry »